The Most Terrifying Risk to the United States Utilities, Tech Corporations, and Department of Defense Agencies (It is NOT Russia or China)
In my 19-year career, as a high-tech consultant, I have had unprecedented access to the Operational Support Systems that manage and control the IT infrastructure of several government agencies, and Fortune 100 companies based in the United States. My role, on several occasions, was to architect, deploy, and integrate Operational Support Systems (OSS). On several occasions, my role was Configuration Management Architect, and/or Systems Analyst.
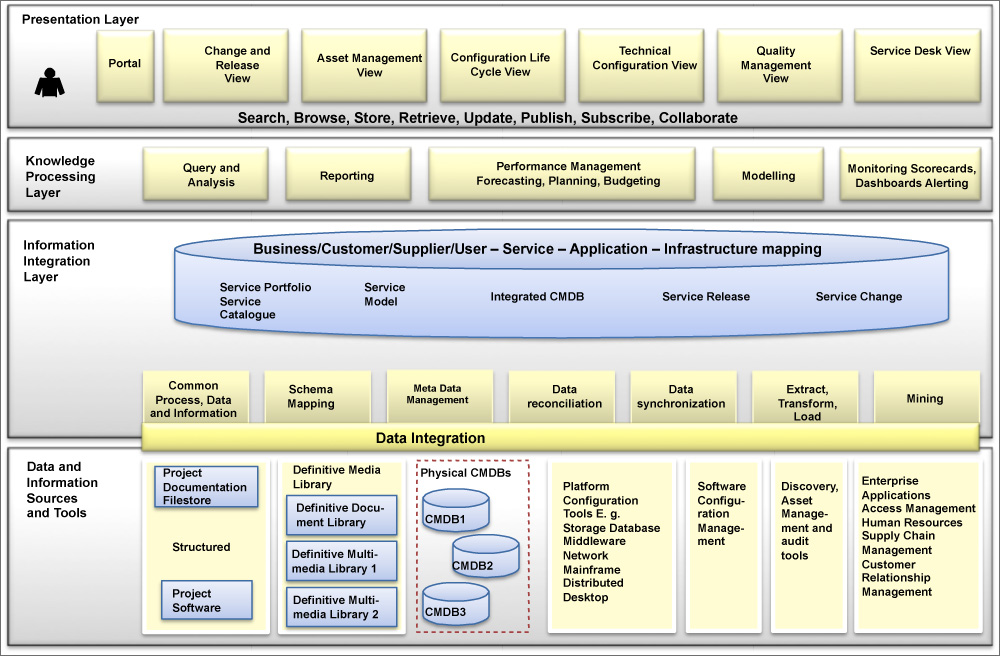
OSS is a set of management systems and tools used to manage operations capabilities of organizations. OSS is an integral part of the larger Telecommunications Management Network (TMN) framework, which encompasses both OSS and Business Support Systems (BSS).
The primary functions of the OSS is to monitor, control, analyze, and maintain network infrastructure, and other systems that provide services to an organization. These systems play a critical role in ensuring the smooth functioning of the network and delivering high-quality services.
Key components and functionalities of Operational Support Systems include:
- Fault Management – These systems monitor the network for faults and issues, identifying potential problems and alerting the network operations center(s) (NOC). It helps in quick detection, isolation, and resolution of network failures and anomalies.
- Performance Management – These systems monitor the performance of network elements and services, analyzing data, and ensure the network operates at optimal levels. It helps identify bottlenecks and areas for improvement.
- Configuration Management – These systems track and manage the configuration details of network devices, ensuring consistency and accuracy of configurations across the network.
- Inventory Management – These systems are used to to manage inventory of network resources, including physical equipment, logical components, and software licenses. It helps with capacity planning and resource optimization.
- Security Management – These systems handle security-related aspects of the network, including access control, authentication, and authorization, to protect the network from unauthorized access and potential threats.
- Service Fulfillment – These systems are responsible for service activation and provisioning, ensuring that new services or modifications to existing services are deployed correctly and efficiently.
- Service Assurance – This involves monitoring and measuring the quality of services provided to customers, ensuring that service-level agreements (SLAs) are met.
- Billing and Accounting Integration – OSS often interfaces with BSS to ensure accurate billing and accounting for the services used by customers.
By streamlining and automating various operational tasks, OSS helps reduce operational costs, enhance network performance, improve customer experience, and accelerate the deployment of new services. It plays a crucial role in managing the complex and dynamic nature of modern telecommunications networks.

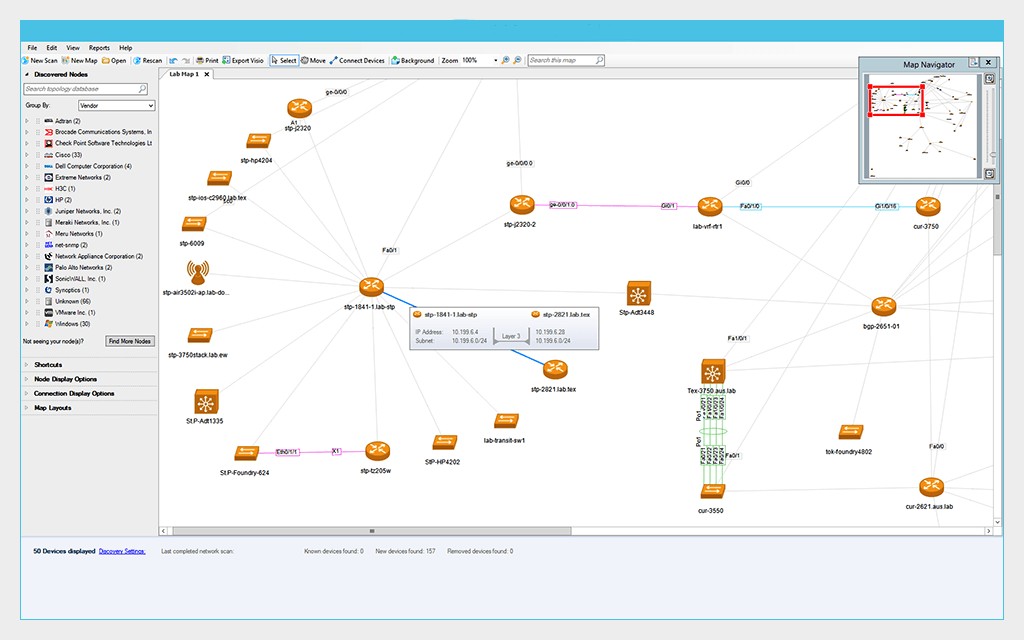
Network Configuration Management Systems (NCMS) are software tools or platforms designed to help IT professionals and network administrators efficiently manage and control the configurations of networking devices within an organization’s network infrastructure. These systems play a crucial role in ensuring the stability, security, and proper functioning of the network.
Configuration Management is the process of provisioning the configurations of all of your network devices across an entire organization, such as Cellular Companies, Electric Utilities Companies, Department of Defense Agencies, the DISA SIPRNET, or any other critical infrastructure provider.
Here’s an overview of what network configuration management systems do:
- Configuration Backup and Versioning – NCMS captures and stores the configurations of network devices, such as routers, switches, firewalls, and load balancers. It maintains version histories of these configurations, allowing administrators to roll back to previous configurations if needed.
- Centralized Management – NCMS provides a centralized interface from which administrators can view, modify, and apply configurations across multiple devices throughout the network.
- Configuration Change Tracking – The system tracks all configuration changes made to network devices. This audit trail helps identify who made specific changes and when, enhancing accountability and aiding in troubleshooting.
- Configuration Compliance – NCMS helps enforce network compliance policies and standards by verifying that configurations align with predefined templates or security best practices. Non-compliant configurations can be identified and corrected promptly.
- Configuration Automation – NCMS allows administrators to automate configuration tasks using scripts or templates. This automation saves time, reduces manual errors, and ensures consistent configurations across devices.
- Real-time Monitoring – Some advanced NCMS platforms offer real-time monitoring of network devices. They can detect configuration changes made outside the system and alert administrators of any unauthorized modifications.
- Change Management Workflow – For large organizations with multiple administrators, NCMS often includes change management workflows. This process helps control access to configuration changes, ensuring that only authorized personnel can modify critical settings.
- Disaster Recovery and Rollback – In the event of a network failure or breach, NCMS can facilitate rapid disaster recovery by restoring configurations to a known, stable state.
- Reporting and Analytics – NCMS generates reports and provides analytics on network device configurations, helping administrators gain insights into the overall health and performance of the network.
- Integration with Other Systems – Some NCMS platforms integrate with other network management tools like monitoring systems, security information and event management (SIEM) platforms, and IT service management (ITSM) systems, enhancing the overall efficiency and effectiveness of network operations.
Overall, network configuration management systems are essential tools for maintaining network stability, security, and efficiency, making them a vital component of any modern IT infrastructure.
The Problem
The biggest threat to our critical infrastructure is one or two individuals that have administrative access to a core Configuration Management System. One person can literally deploy corrupt configurations to every network device of an agency, on a global scale. A simple set of command scripts could issue password changes, firmware deployments, and provision corrupt configurations to the “startup and run” configurations of every network device.
Let’s take a main cellular company, for instance. If one rogue administrator with the right access decided to perform this deployment corrupt configurations, it could bring down the entire company’s ability to operate for days, or even weeks.
Years ago, I wrote several reports on this topic and delivered my findings to military officials, and security experts in the industry. One of these people was a personal friend. The whole topic was quietly swept under the rug, because no one wants to address potential problems as serious and sensitive as this.

Redirection
Most of us have read somewhere or watched a video talking about threats to our critical infrastructure and how we could be attacked by Russia, China, Iran or some other villain they want you to direct your interest toward. The fact is that the biggest potential threats are from inside, and not from some external boogeyman.
Conclusion
The susceptibility of the United States’ critical infrastructure to attacks from within poses a significant and alarming threat to the stability and security of our nation. Specifically, Configuration Management Systems are where the biggest risk resides, if a single rogue administrator decides to initiate a planned attack. Whether through insider threats, compromised employees, or unintentional errors, the consequences of such attacks can be devastating, disrupting vital services and compromising sensitive data. Today, the lax screening processes and second-rate hiring practices have become so bad, there is a strong possibility that there are currently rogue individuals already sitting in these very sensitive, high level technical positions. To safeguard our critical infrastructure, a multifaceted approach is required, encompassing robust security protocols, continuous monitoring, proper screening process for access, and a proactive stance against potential threats. Creating a strong and reliable screening process for security, is crucial for maintaining the safety and integrity of a system or organization. Only by acknowledging and addressing the vulnerabilities within our own ranks can we fortify our critical infrastructure against the ever-evolving landscape of internal risks and external adversaries.